Ethical hacking, an essential practice for maintaining the security of networks and systems, has gained immense significance in today’s digital age. As cyber threats evolve, so too must the tools and techniques used by ethical hackers.
One of the primary differences between talented hackers and novices is knowing how to use the tools at their disposal. Anyone can download Kali Linux or Parrot OS and use the tools out of the box but it takes dedication and research to utilise these tools fully and knowing when and where to use them for full effect.
With that in mind this article highlights the top tools every ethical hacker should be familiar with, drawing from industry insights and expert opinions.
1. Metasploit: The Swiss Army Knife of Hacking Tools At the forefront is Metasploit, a powerful penetration testing framework that enables hackers to discover vulnerabilities, write and test code, and execute attacks. It’s a must-have for its versatility and extensive database of exploits.
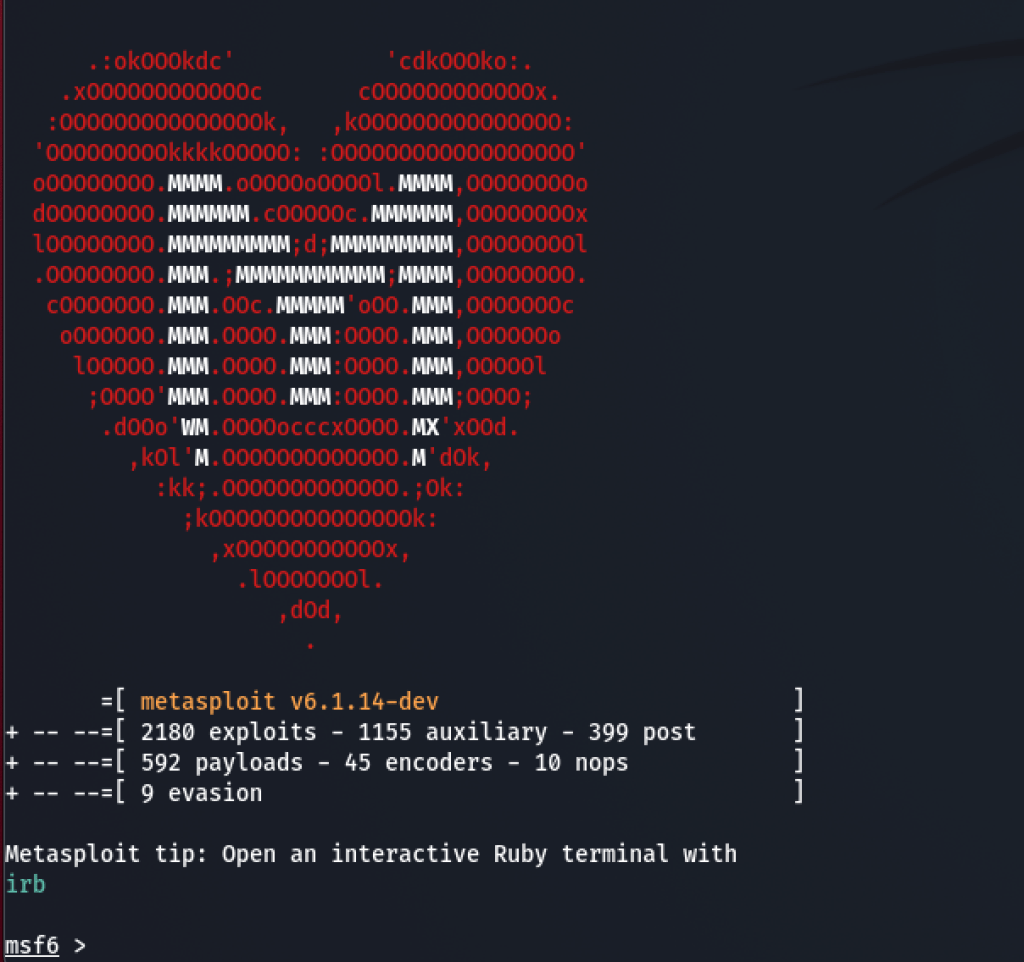
Metasploit is built with Ruby and comes with an insane amount of modules that perform essential tasks for the modern day ethical hacker from scanning targets, delivering vulnerable code, managing open connections to pwned systems and even post exploitation modules. It is a tool that must be mastered by any aspiring hacker today.
2. Wireshark: The Network Traffic Analyst Wireshark is renowned for its ability to analyse network traffic in real-time. Its detailed packet analysis capability is crucial for understanding network protocols and identifying suspicious activities.
The great thing about Wireshark is it can be used for network admins as well as hackers. It’s ability to capture and analyse packets can aid in finding faults or network choke points. It is a versatile tool that should not be underestimated.
3. Nmap: The Network Mapper Nmap excels in scanning and mapping network infrastructures. It helps in identifying open ports, detecting devices running on a network, and uncovering services and applications.
This is the first tool I use when performing a penetration test or start on a new bug bounty target. The information gleamed is general but absolute gold and can tell you where the low hanging fruit is on a target.
4. Burp Suite: The Web Vulnerability Scanner For web application security, Burp Suite is the go-to tool. It offers comprehensive solutions for scanning, testing, and exploiting web applications, making it a favourite among security professionals.
Burp Suite is a brilliant tool, you can capture requests and modify them, brute force credentials, decode hash’s. For web app testing Burp is invaluable.
5. Kali Linux: The Ethical Hacker’s OS Kali Linux, a Linux distribution designed for penetration testing and security auditing, is packed with hundreds of tools catering to various information security tasks. It’s the preferred OS for most ethical hackers.
There’s a reason Kali is the most popular pen testing OS. I’ve tried Kali, Parrot and had a stint using Black Arch but Kali is not only the easiest(in my opinion) but it offers a huge amount of tools and is incredibly versatile. However my favourite part about it is the community. There is not an issue that someone else hasn’t already come up against and found a work around or solution.
6. Aircrack-ng: The Wireless Network Hacker Focusing on wireless network security, Aircrack-ng is a suite of tools for Wi-Fi network security assessment, including tools for monitoring, attacking, testing, and cracking Wi-Fi networks.
7. John the Ripper: The Password Cracker John the Ripper is a fast password cracker, ideal for detecting weak passwords. It supports numerous encryption formats and is instrumental in enforcing strong password policies.
8. Nessus: The Vulnerability Scanner Nessus is widely used for vulnerability scanning. It helps in identifying vulnerabilities, misconfigurations, and potential risks in networks and systems.
9. OWASP ZAP: The Web App Pen Tester The OWASP Zed Attack Proxy (ZAP) is an open-source web application security scanner. It’s designed to find a variety of security vulnerabilities in web applications while they are in development and testing phases.
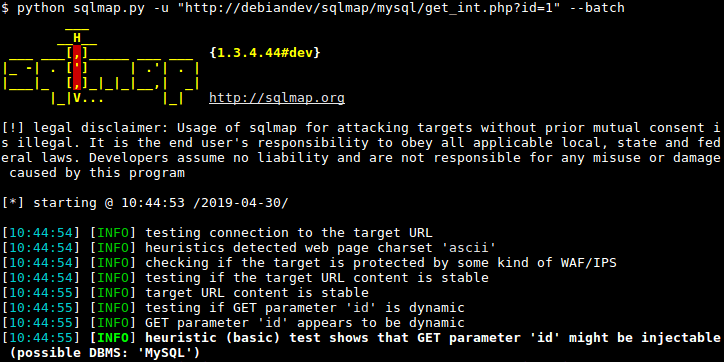
10. SQLmap: The Database Exploiter For database security, SQLmap automates the process of detecting and exploiting SQL injection flaws. It supports a wide range of database servers and can retrieve database information, running commands on the operating system via out-of-band connections.
These tools represent the crux of an ethical hacker’s toolkit, providing them with the capabilities to assess and fortify cybersecurity defences effectively. However, it’s crucial to remember that the landscape of cyber threats is continually evolving, and staying updated with the latest tools and techniques is paramount in the field of ethical hacking.




Leave a comment